Microsoft announced the availability of Microsoft Entra Suite, which will compete in the hot security service edge (SSE) market.
Microsoft’s domination of the enterprise software market means that many organizations will “end up” with Microsoft solutions, even if that’s not what the CIO or CISO really wanted. Take Microsoft Teams; because it’s Microsoft, it’s everywhere. If you’ve talked with me lately, for example, it was probably over Teams. A more constructive, less divisive example is Sentinel, which rocketed into the security operations market and took significant market share. The point is, when Microsoft enters a market, the vendor can very quickly take market share.
Microsoft Entra Suite, at these reasonable retail prices, will put intense pressure on the SSE market leaders. The smaller SSE vendors will have to retire, run for cover, or reinvent themselves. The Microsoft Entra Suite includes:
-
- Microsoft Entra Private Access
- Microsoft Entra Internet Access
- Microsoft Entra ID Governance
- Microsoft Entra Verified ID (premium capabilities)
- Microsoft Entra ID Protection
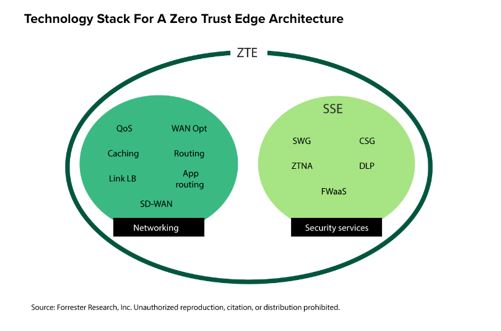
SSE Primer
In evaluating an SSE stack, we identified three security technologies as primary and several as secondary. These include:
- Zero Trust network access (ZTNA) to control access to private hosted applications.
- Cloud access security broker (CASB) to control access to public internet applications and services.
- Secure web gateway (SWG) to protect against the big bad scary internet (everything else).
Each of these technologies evolved during different eras. The SWG is an ancient tech from the ’90s (!) that has had exactly one significant innovation in 25 years (cloud delivery). CASB evolved a decade later, after cloud, to help control access and prevent loss among the thousands of cloud services. ZTNA hit its stride during the pandemic, replacing VPNs and giving everyone a taste of Zero Trust honey. Secondary technologies, like data loss prevention (DLP) and remote browser isolation (RBI), augment these primary technologies. See our full report on SSE to learn the value of SSE and how to evaluate offerings.
Today, few customers are interested in any of these technologies as stand-alone. They only make sense when bundled together, with a single local software agent authenticating, securing, and directing connections appropriately.
Deconstructing The Microsoft Entra Suite Offering
The Redmond, WA giant’s conditional access has been upgraded to a full-featured paid service called “Private Access” to provide Zero Trust access (ZTA) to your applications. Perhaps acknowledging market leader Zscaler’s dominance in ZTNA right now, Microsoft’s local software agent is built in such a way as to coexist with Zscaler’s ZTA (and presumably everyone else’s ZTNA, too).
Microsoft already has a market-leading CASB. It isn’t part of the Microsoft Entra Suite, but you can, of course, get it separately or with E3 and E5 security.
New for the offering is Microsoft Entra Internet Access, Microsoft’s version of a cloud-delivered SWG. As it is new, expect this to be the weakest link in the chain (for now), offering fewer features than competitors with more bumps and warts exposed.
Taken individually, by any other vendor, none of these offerings would excite the market. The fact that they are offered by The Redmond Giant is the significant thing.
Interestingly, and cleverly, Microsoft is positioning these with three identity offerings. The suite promotes Microsoft Entra ID Governance (an identity governance and administration offering), Microsoft Entra ID Protection, and Microsoft Entra Verified ID (a face check). Microsoft isn’t the only vendor doubling down on “identity” as a pillar of cybersecurity: You’ll see others, like Cisco Systems, considering a similar focus. As generative AI drives phishing attacks to a new level of sophistication, these identity technologies will be in high demand.
Use The Coming Market Pressure To Capture Value
The general availability release of Entra Suite will put massive pressure on all the SSE vendors. The smaller vendors will have to run for cover: Expect fire-sale acquisitions to larger infrastructure vendors, bankruptcies, and radical specialization in particular verticals such as operational technology or healthcare.
Clients who are looking at SSE solutions should use the market pressure to get good deals with the large, existing SSE vendors. Those considering a smaller SSE vendor should take pause and ensure that they can back out of that solution if it can’t weather the coming storm.
We haven’t evaluated the full Microsoft Entra solution, so we won’t make a recommendation on it other than to say that parts of it (especially the SWG and aspects of private access) are brand-new and should be thoroughly tested in your environment.
ZTE/SASE Champions: Stay The Course
Clients adopting the whole Zero Trust edge (ZTE) or secure access service edge (SASE) architecture should ignore the Microsoft product (for now) and stay the course. ZTE/SASE has massive network capabilities and requirements, and Microsoft has nothing here yet, nor is it likely to do anything more than technical partnerships. But we continue to advocate for single-vendor ZTE/SASE to take advantage of a single user interface, a single network, and a single data lake for both networking and security.
Ask Me About SSE
The Forrester Wave™: Security Service Edge Solutions, Q1 2024, evaluates SSE providers (but doesn’t include Microsoft, since it had not yet entered the market). Forrester clients who want to pick my brain directly should set up an inquiry or guidance session with yours truly, and we can talk about SSE, Microsoft Entra Suite, secure access service edge, ZTE, or anything else in my coverage areas.