I can see clearly now the noise is gone! As Zero Trust mandates begin to creep into the private sector, organizations are tasked with the seemingly impossible: observe and inspect all network traffic regardless of direction (N/S/E/W), encryption, or location within the enterprise. One cannot rely on metadata alone, nor slap an endpoint technology in place and say, “Boom, network security!”
My new report, The Modern Definition of NAV, discusses the features of robust Network Analysis & Visibility (NAV) instantiations, and why visibility is imperative in today’s insecure world.
Zero Trust Requires Network Visibility and Analytics
Network visibility—the ability to gain comprehensive insights into the traffic, devices, and users traversing the network environment – is a critical part of the Zero Trust framework. Network visibility enables organizations to monitor, analyze, and understand the myriad interactions occurring within their on-prem, cloud, and hybrid infrastructures. This insight allows organizations to detect anomalies, identify potential threats, and enforce granular access controls in real-time without console hopping and searching the internet for CVEs and IoCs.
Forrester defines NAV as:
Security tools that deploy passively in networks to analyze network traffic to detect threats using behavioral and signature-based approaches; discover and establish relationships between assets; analyze traffic flow; extract relevant metadata; enable full or targeted packet capture; integrate with other control points to respond to detected threats; and enable network forensics.
When combined with a robust AI/ML, NAV technologies provide relief to overworked SOC analysts by:
- Filling in toolset gaps. NAV delivers detailed analysis and correlation of telemetry feeds from adjacent technologies, such as XDR, NGFW, Proxies, and ZTNA solutions for a single source of truth on the network.
- Painting a comprehensive picture of the network. Today’s networks are an amalgamation of on-prem, hybrid, and cloud topologies, with applications and data repositories scattered about like a windy autumn day. NAV helps to make sense of the networks, dependencies, and assets, to provide a clear picture of what lurks beneath the surface.
- Exposing hidden risks in encrypted traffic. Approximately 91% of threats utilize encryption to obfuscate the payload. NAV provides insight into encrypted streams via native decryption, or secure ingestion of decrypted streams, allowing the truth to be exposed without reliance on packet behavior as the sole indicator of a malicious event.
NAV Is Part Of The Visibility And Analytics Domain In Zero Trust
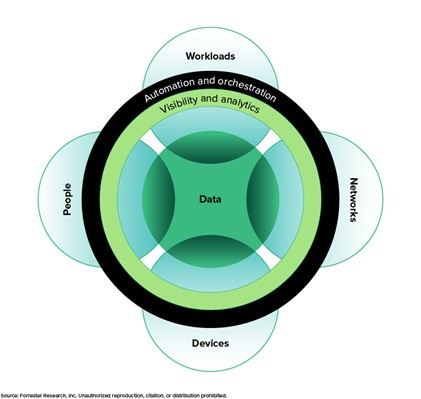
The importance of network visibility in the Zero Trust framework cannot be overstated as organizations navigate the complex digital landscape rife with cyberthreats. By embracing a model where trust is earned through continuous validation and verification and leveraging robust network visibility solutions to gain insights into their infrastructure, organizations can fortify their defenses, mitigate risks, and safeguard their most valuable assets. NAV technologies serve as a beacon of clarity, illuminating the path towards a more secure and resilient future.
Learn More
Forrester clients can schedule an Inquiry or Guidance Session with me to learn more about getting visibility with NAV and enabling Zero Trust.