Cybersecurity breaches are still on the rise, impacting organizations of all sizes, sectors, regions, and industries. Despite continued investments in security technologies, processes, and resources, the ever increasing complexity of cyber threats continue to challenge even the most robust security teams.
Our latest research analyses the 100 most notable global breaches from 2023 to distill patterns, uncover nuances, and identify the top lessons all organizations must pay attention to. We also saw eight common incident types.
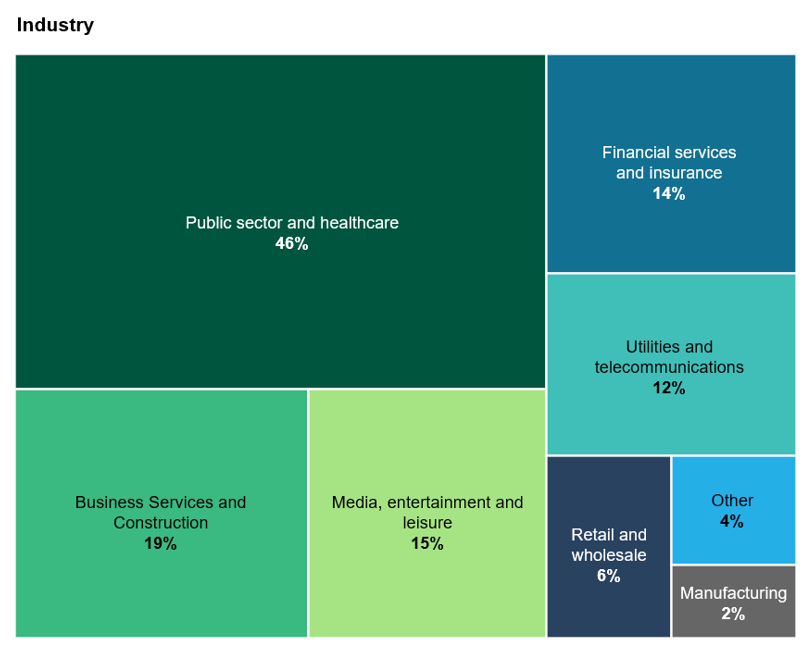
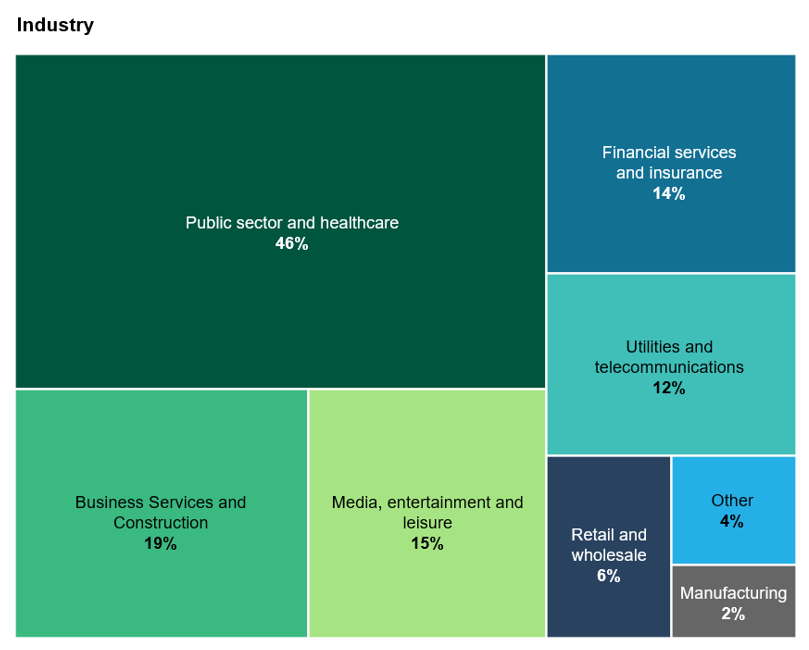
Tech execs should use lessons learned from the top 100 to tighten their practices in their security programs to avoid befalling similar issues. We found that:
- For many breaches, the root cause remains a mystery or is never publicly revealed. Among the most startling revelation from our research is the high number of breaches where the root cause remains This trend is especially prevalent in APAC, where breach notification laws and practices are still developing, as well as in EMEA. North America shows a different pattern, with third-party vulnerabilities, indicating a focus on supply chain weaknesses by attackers. Security leaders must prioritize identifying and reporting the root causes of breaches to develop more effective prevention strategies and comply with regulatory requirements.
- Third parties are still your weakest link. Third-party vulnerabilities have an outsized impact on four of the seven industries with larger enterprises more affected by third-party vulnerabilities than smaller mid-sized firms. While this may seem counterintuitive, larger enterprises have larger third-party ecosystems meaning they have a larger set of suppliers who could offer an entry-point. Attackers have favored exploiting weaknesses in suppliers to large organizations with access, over attacking them directly due to the weaker security practices seen in many suppliers.
- Weak and stolen credentials, are a nightmare for smaller firms. Firms at the small end of town were disproportionately affected by breaches involving weak and stolen credentials. These incidents often stem from misconfigurations, lapses in identity governance, and credential reuse. Smaller organizations often have smaller security budgets, frequently do not have their own security departments, but are important links in larger supply chains. Third-party and supply chain risk impacts shows the critical importance to ensure smaller entities are secured.
- Social engineering continues to be a timeless classic. Social engineering remains a favored technique for cybercriminals, leveraging human fallibility to gain unauthorized access. While its overall incidence decreased, it remains a significant threat, especially with the advent of generative AI tools that can craft more convincing phishing messages, and break down language barriers – for example, Japan has recently seen a 35% year-over-year increase in BEC attempts. Firms really have no option but to nail the basics of email and collaboration security, and managing the human risk.
This was only a small portion of the report’s findings. If you are interested in finding out more, read the report or reach out to me or any of my coauthors for inquiries or guidance sessions.